How to Resolve Common Microsoft Entra Connect Errors: A Tale of TLS and Tiny Disks
This morning while I was sipping my tea, I pondered life’s most important question: “Why aren’t my users synchronizing from my on-premises Active Directory to my Microsoft Entra ID tenant?”
During my initial Password Hash Sync attempt, my synchronization service account was created, but none of the users synchronized, and the installation service timed out with this error:
“An internal problem has occurred. It appears that you are resuming a scenario that was not completed previously during installation. Please uninstall and try again.”

Seems simple enough. Maybe just a timeout error? Dutifully following the instructions, I uninstalled the Microsoft Azure Active Directory Connect agent along with all references to it. I also checked the registry to ensure that the product was no longer listed.
Then I attempted the installation/synchronization again.
And again.
And again.
Each time I encountered the same error, “Please uninstall and try again.”
No matter how many times I begged the wizard, it would not let me pass or give me a more specific error message.
My colleague suggested resizing the virtual machine, which was a great idea since I had picked the cheapest option available. Technically my VM did not meet the prerequisite requirements for running AD Connect, since the following sizes are required:
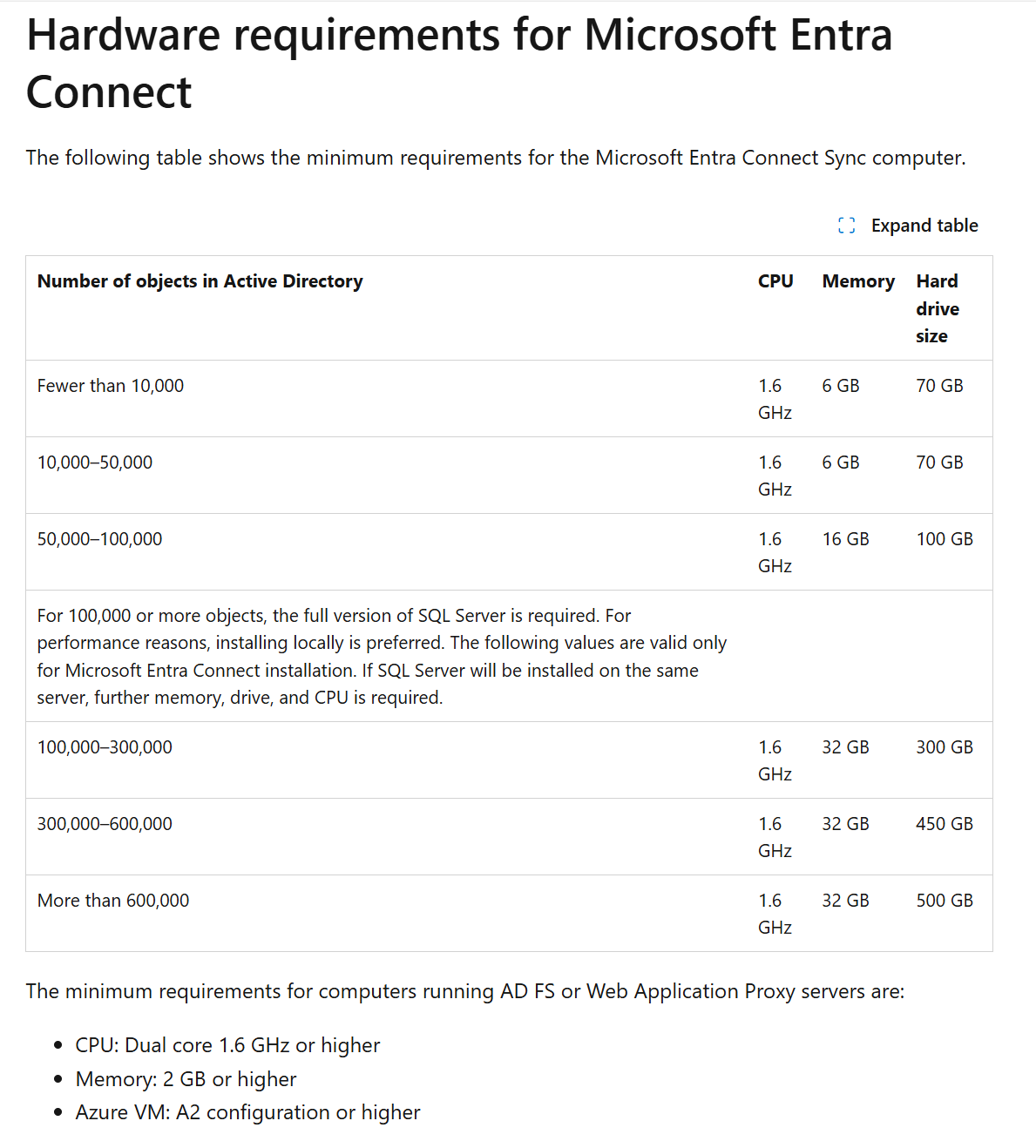 Reference: Microsoft Entra Connect: Prerequisites and hardware — Microsoft Entra ID | Microsoft Learn
Reference: Microsoft Entra Connect: Prerequisites and hardware — Microsoft Entra ID | Microsoft Learn
I had been following a separate set of installation instructions and forgotten to check the general prerequisites for Microsoft Entra Connect. Always a good idea to check those first.
After resizing the VM to a Standard_E2S_V3 series, the installation ran much faster. However, the process still failed with the same error: “Please uninstall and try again.”
The trace log revealed these equally generic errors:
No registered products found. ServiceControllerProvider: InvalidOperationException on serviceController.Status property means the service ADSync was not found Product Azure AD Connect Synchronization Agent is not installed. An error occurred executing Configure AAD Sync task: An error occurred while sending the request. Failed to read DisplayName registry key: An error occurred while executing the ‘Get-ItemProperty’ command. Cannot find path ‘HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MicrosoftAzureADConnectionTool’ because it does not exist. ExecuteADSyncConfiguration: configuration failed. Skipping export of synchronization policy. resultStatus=Failed [ERROR] PerformConfigurationPageViewModel: We encountered a problem and couldn’t complete the integration.
After some Binging, I came across a recommendation to ensure that Windows Server 2019 machine had TLS 1.2 enabled. I thought this suggestion was a long shot, since it is standard for supported Windows Server machines to have TLS 1.2 enabled by default.
But I ran this PowerShell script to check the TLS settings, and sure enough, TLS 1.2 “Enabled” was set to “Not.”

I checked the registry to see if the TLS 1.2 keys existed, and they did not. So I ran this PowerShell script to enable TLS 1.2.
Next I rebooted the machine and ran the installation again. This time, however, I decided not to check the box for “Start Synchronization.” I wanted the installation to complete without over-stressing the poor VM to run the sync at the same time.
These steps seemed to help. When the installation finished, rather than running into the same installation loop, I encountered a brand-new error!
“The synchronization service scheduler is suspended until this setup wizard is closed. Learn more about ‘Scheduler and installation wizard.’”
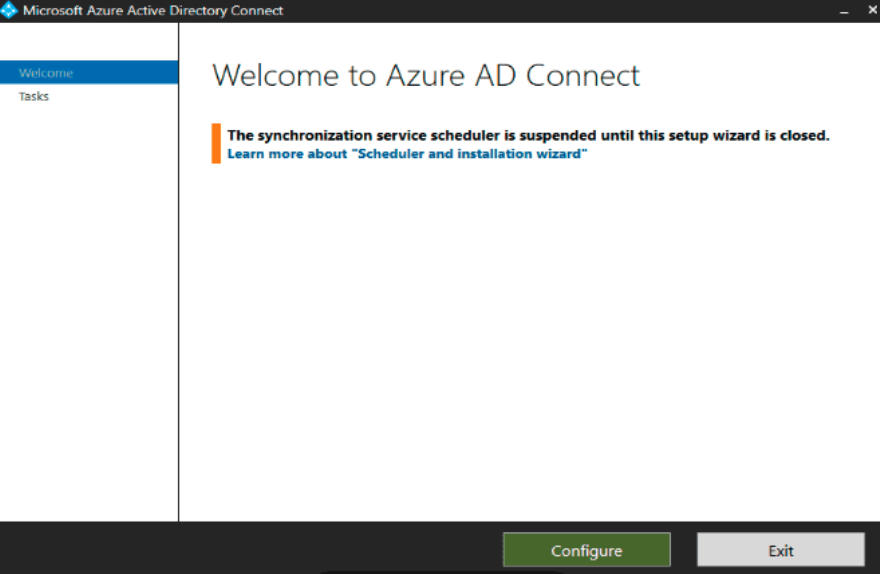
I searched the error and found that it usually occurs when the synchronization service detects that the synchronization is happening, but it does not want you to open the Microsoft Entra Connect/Azure AD Connect tool to make changes.
A way around this issue is to start the synchronization service and run a Delta sync.
I then ran these two PowerShell commands:
Set-ADSyncScheduler -SyncCycleEnabled $true Start-ADSyncSyncCycle -PolicyType Delta
After running these commands, my synchronization completed successfully, and all of my users appeared in my Entra ID tenant!
If I had started out with a properly sized VM with TLS enabled, I probably could have avoided many of these errors and had a smooth installation. But hopefully my mistakes will help others get past these common Microsoft Entra Connect errors.
